Deshare Trusted Chips
The Challenge
For years, connecting real-world devices to blockchain has relied heavily on centralized cloud services or manual data reporting — creating weak links in trust. Data could be delayed, manipulated, or unverifiable. In the DePIN and RWA ecosystem, this meant that "on-chain" data often wasn't truly trustless.
Deshare 2.0 was built to change that — enabling verifiable data provenance and on-chain authentication starting directly from the device itself.
The Solution
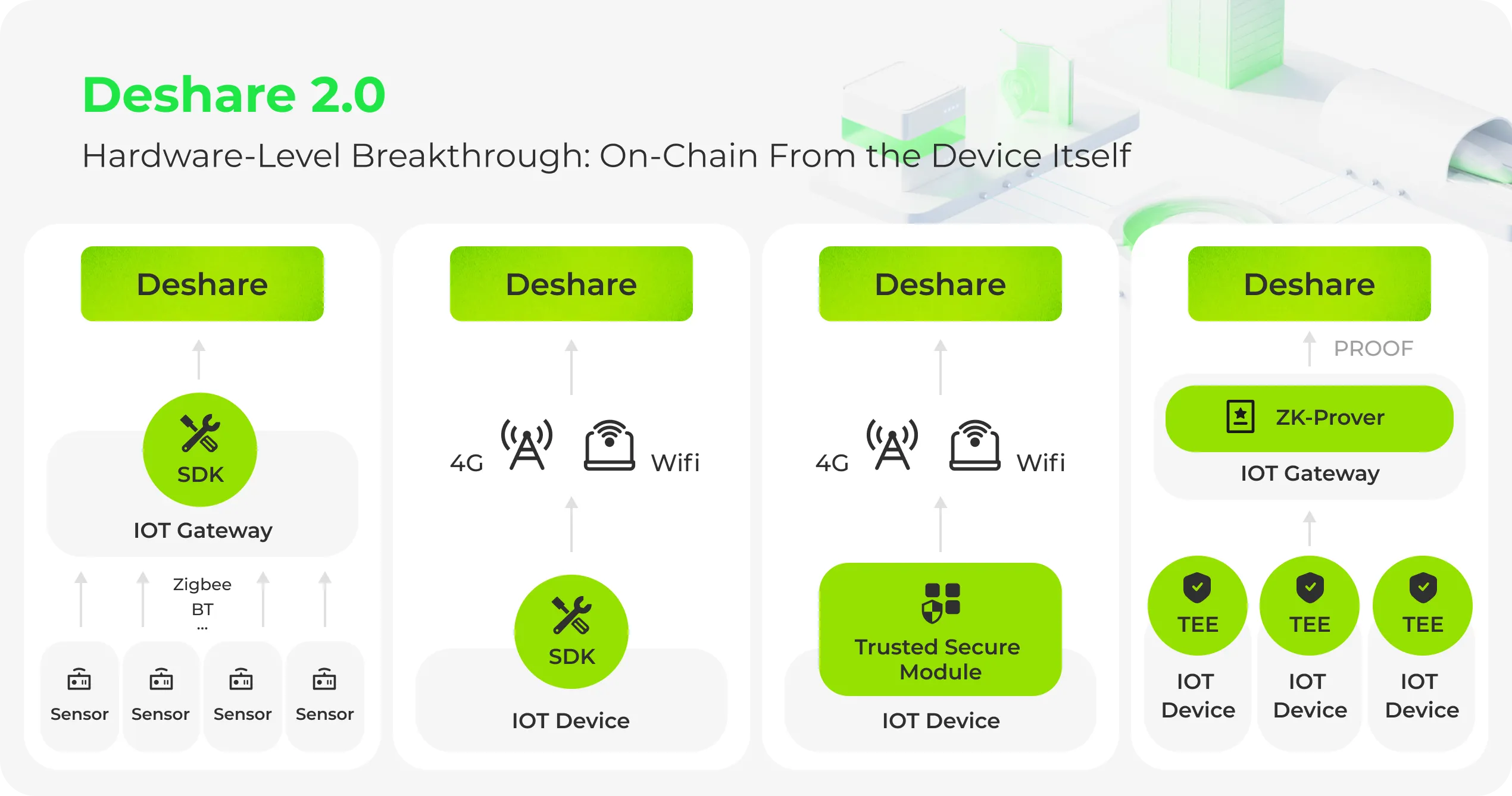
Deshare 2.0 introduces a multi-layer hardware-to-protocol integration architecture, designed to bring trust, flexibility, and scalability across different types of connected devices. Without changing existing hardware or disrupting ongoing operations, Deshare enables brands to anchor real-world data onto the blockchain — creating verifiable digital assets from physical usage.
We've built four complementary integration modes that fit different device types and technical environments:
1. Cloud Gateway Adaptation (for legacy IoT systems)
Designed for brands already operating large fleets of IoT devices connected via centralized cloud systems. Deshare provides a cloud adapter layer that intercepts, verifies, and standardizes key operational data before anchoring it to the Deshare Protocol.
- No hardware modification required
- Rapid deployment across existing IoT fleets
- SDK/API available for seamless data mapping
2. Edge-Side SDK Integration (lightweight & modular)
For partners seeking device-level data signing without hardware redesign, Deshare offers a lightweight embedded SDK for integration into terminal or edge gateways.
- Generates verifiable device identity and cryptographic signatures locally
- Anchors data hashes to the blockchain via Deshare Protocol
- Ideal for smart terminals like power banks, vending machines, EV chargers, or energy meters
3. Trusted Hardware Integration (advanced security layer)
Deshare also supports a Trusted Secure Module (TSM) integration for partners requiring hardware-grade trust. The TSM can be embedded into the mainboard or connected through standard interfaces (UART, SPI, or I²C) to handle key management, data signing, and encrypted communication. This provides hardware-level verifiability without full hardware redesign — ideal for OEMs aiming to make their devices "Web3-ready by design."
- Private keys are generated and stored securely within the chip
- On-device signing for all events or transactions
- Secure communication with Deshare Protocol, preventing spoofing or tampering
4. TEE & ZK Integration (future roadmap)
Looking ahead, Deshare will integrate TEE (Trusted Execution Environment) and ZK (Zero-Knowledge Proof) technologies to achieve privacy-preserving trust verification. In this model, devices will not only sign data but also prove their operational integrity — confirming that reported data originates from genuine device activity without exposing raw information. TEE ensures isolated, tamper-resistant computation, while ZK enables the generation of verifiable proofs validated on-chain. Together, they pave the way for autonomous, privacy-preserving DePIN networks where devices can prove their performance, energy output, or usage metrics in a trustless manner.
How It Works
When a device records an event — such as a charging session, energy output, or usage transaction — Deshare captures the essential metadata (device ID, timestamp, transaction hash) and generates a cryptographic proof.
That proof is transmitted via the chosen integration mode (cloud adapter, SDK, TSM, or TEE-secured endpoint) and anchored on-chain through the Deshare Protocol. Each verified data point becomes a Verifiable Device Event (VDE) — a standardized, traceable data primitive that powers downstream applications including:
- Transparent RWA revenue distribution
- Usage-based DePIN incentive models
- Cross-brand settlement and analytics
With Deshare 2.0, every connected device becomes a trust anchor — transforming the physical world into a verifiable digital layer of the Web3 economy.